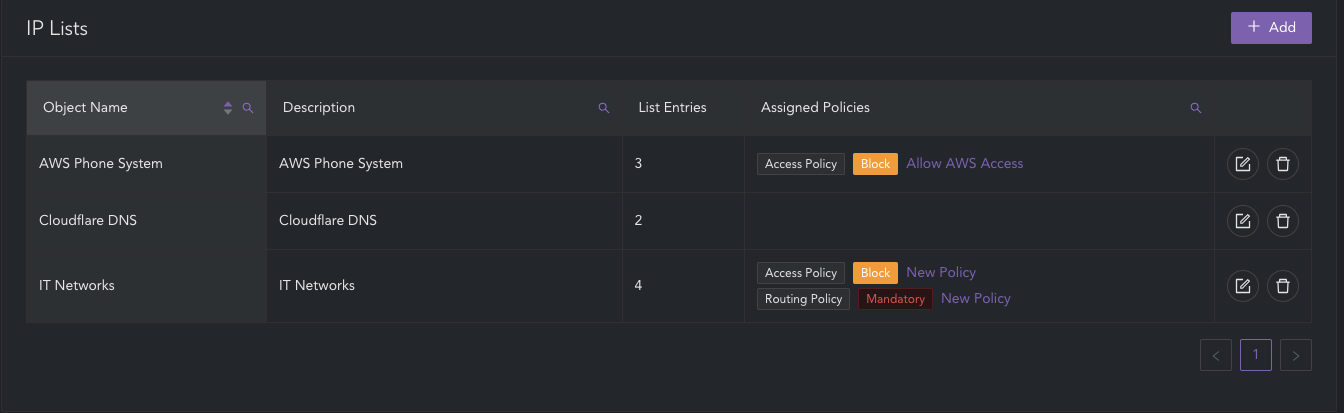
IP Lists
An IP List is a collection of IP addresses, networks, or ports organized for streamlined management and reference within the CyberEdge configuration. By creating object lists, administrators can centralise and reuse these sets across various policies, including Access Policies, Fast Path Policies, Routing Policies, and others. This method simplifies the configuration process, improves consistency, and reduces the effort needed to maintain policies. When applied, changes made to a list are automatically reflected wherever the object is used.
IP List Types
IP List Types determine where the associated list object can be referenced within the configuration. Setting the correct IP List Type is important to avoid unnecessary configuration rework. The IP List Types include:
-
Source List: Source should be used when the list is required in the Source Network criteria of a policy.
-
Destination List: Destination should be used when the list is required in the Network Destination criteria of a policy.
-
Unspecified List: Unspecified should be used when the list is required in both the Network Destination and Source Network criteria of a policy.
Note
- Source and Destination IP List Types will be available in all Policy configurations including Access Policies, Fast Path, Traffic Shaping, Routing and Roamsafe Agent Policies.
- In a future release, unspecified IP Lists will be accessible in additional sections of the CyberEdge configuration.
- Changes made to IP lists will be automatically reflected in all policies that reference the list.
Supported IP Ranges
IP Range inputs offer flexible options for list creation, streamlining network administration. The following examples demonstrate the supported (validated) configurations for defining IP ranges, which are particularly useful for managing large or complex lists. Supported configuration examples include:
-
Single IP Address
10.10.12.50 -
Network Subnet (CIDR)
10.10.12.50/32 -
IP list
10.10.12.51 10.10.12.52 10.10.12.53 -
IP Ranges
10.10.12.50-10.10.12.60 10.10.12.65-10.10.12.80 -
Combined list
10.10.12.50-10.10.12.60 10.10.12.65-10.10.12.75 10.10.12.105 10.10.12.150
Create an IP List
To create a IP list navigate to:
- shared objects > IP/Port Lists > IP Lists
- Click "Add"
- Enter the following:
- Name: The name for the list. This is the name of the object that will be referenced within the UI.
- Description: The description for the list.
- List Type: The IP List Type for the list. This determines where the list will be accessible from.
- IP Ranges: The IP or IPs for the list.
- Click "Save"
- Click and "Save" and "Apply" changes
The object will now be accessible within the CyberEdge Policy source and destination criteria configuration.
Tip
Object names should be clear and concise to avoid accidental misuse by administrators.
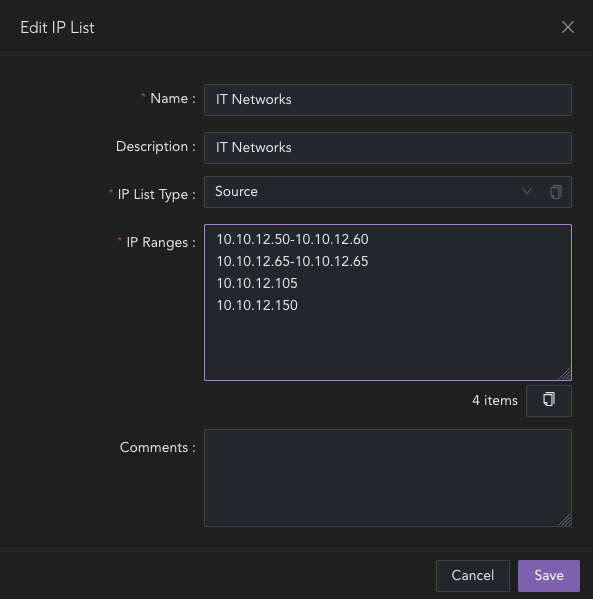
Edit an IP List
To edit an IP list navigate to:
- shared objects > IP/Port Lists > IP Lists
- Click "Edit" on the required list
- Make the required changes:
- Name: Change the object name.
- Description: Change the description for the list.
- IP List Type: Edit the IP list type.
- IP Ranges: Input an IP Address, a list of IPs, range of IPs, or subnet for the list.
- Click "Save"
- Click and "Save" and "Apply" changes
Important
- The List Type is used to determine how and where the object list will be referenced. For example, list types of "Source" will be referenced in the Source Networks criteria whereas list types of "Destination" will be referenced in Destination Networks criteria. This is to ensure that source and destination lists are used correctly when managing policies.
- When IP Lists are in use by Policies, the IP List Type cannot be changed by default. To change the IP List Type, you must first remove the references in the configuration and apply the changes. Alternatively, you can create a new IP List.
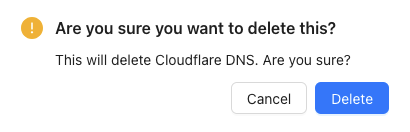
Delete an IP List
To edit an IP list navigate to:
- shared objects > IP/Port Lists > IP Lists
- Click "Remove" on the required list
- Confirm you wish to delete the list.
- Click "Save"
- Click and "Save" and "Apply" changes
If the list is not in use by the CyberEdge configuration
If the list is in use by the CyberEdge configuration, it cannot be removed until all references have been removed.
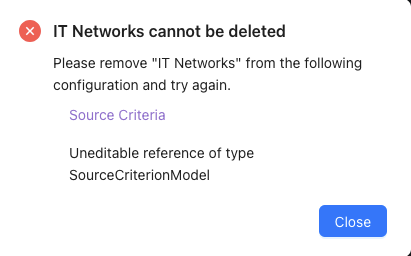
Important
If the list is currently in use within the CyberEdge configuration, it cannot be deleted until all references to it have been removed.