Network Connections
A zone-based network is a security architecture that segments a network into distinct zones, each with its own set of security policies and controls. This approach allows for more granular management of network traffic based on the trust level, function, or the type of data contained within each zone. By default, the CyberEdge provides 4 distinct network zones for which new network connections may be added. These include;
- Internet Zone for WAN/Internet connections
- Local Zone for LAN network connections
- DMZ (Demilitarized Zone), typically used for public-facing networks
- Management Zone, used for access to the management user interface and High Availability replication
Network traffic between zones is controlled by Access Policies. The following network connection configuration guide outlines the process for creating new network connections to the CyberEdge.
Creating a Network Connection
Ethernet network connections provide a standardized approach for establishing connectivity within local area networks (LANs), allowing data packets to be exchanged between devices. Within the CyberEdge framework, networks are categorized into distinct network segments (Zones) based on their function. For instance, an Internet Connection would be allocated to the Internet Zone, while a local Ethernet network would be assigned to a Local or Custom Zone. Crucially, for traffic to undergo inspection processes such as Deep Packet Inspection, Application Control, and Web Filtering, it must pass through a network zone.
To create a Network Connection navigate to;
- Networks > Connections > Add > Network Connection
- Configure the network connection
- Name: The name of the network connection. This name object will referenced throughout the UI.
- Network Adapter: The physical or virtual adapter/port to be used by the network connection
- Network Zone: The network zone segment to be used for the network connection. Eg. Internet Zone or Local Zone
- Traffic Shaping Profile: Apply a traffic shaping profile to the network connection. Default to none
- DHCP configured: Disable/Enable DHCP for this connection. Enabling DHCP will allow the connection to acquire its configuration from DHCP.
- IPv4 Networks: Specify a list of IP networks for your network connection. This field requires a standard IPv4 CIDR format
- IPv4 Gateway: The IP gateway for your network connection. This field requires a standard IPv4 address format
- IPv6 Networks: Specify a list of IPv6 networks for your network connection. This field requires a standard IPv6 CIDR format
- IPv6 Gateway: The IPv6 gateway for your network connection. This field requires a standard IPv6 address format
- Click "Save"
- Click "Save and Apply changes"
The network connection will now be available via Networks > Connections,located within the configured network zone. To move a network connection to a different zone or make changes such as the assigned port, modify a network connection. To modify a network connection navigate to;
- Networks > Connections > Edit
- Make the required such as changing network zone or assigned port
- Click "Save"
- Click "Save and "Apply changes"
Tip
- By default, network connections added to the Internet Zone are not automatically added to the Balance and Failover configuration options. To configure Balance and Failover go to Routing > Balance and Failover
Static Route
A static route is a manually configured network route that specifies a fixed path for data packets to travel within a network. Unlike dynamic routes, which are automatically adjusted by routing protocols, static routes are set by a network administrator to direct traffic through specific paths based on predetermined criteria. To configure a static route, navigate to;
- Networks > Connections > Edit the connection you are adding the route to > Add Static Route
- Configure the Static Route
- Description: A brief name of the route you are creating
- Destination: The destination subnet for the route. This field requires a standard IPv4 CIDR format
- Gateway: The IP address of the gateway for this route. This field requires a standard IPv4 address format
- Metric: The metric for this route (the lower the metric, the higher priority it gets in the routing table). Please note that this can be left blank, and the system will auto fill.
- Click "Save"
- Click "Save and "Apply changes"
To view the complete routing table, which includes static routes for the CyberEdge, navigate to Status > Routes
Tip
While the use of larger subnets (eg. /8 or /16) can make routing of many subnets easier, it will result in being unable to use any of the subnet in any other network configuration (eg. New network connection, VPN Client Subnet). We recommend that you minimise the scope of your routes to just cover the subnets you currently use.
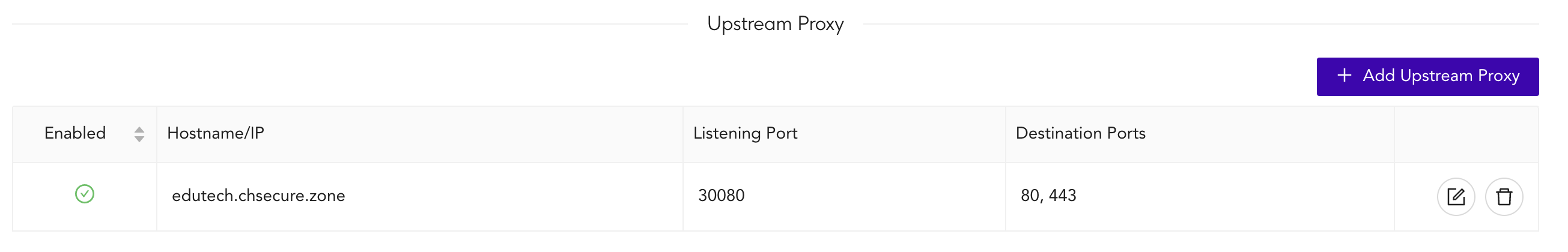
Upstream Proxy
An upstream proxy functions as an intermediary between the CyberEdge and the Internet. When a client device sends a request to the CyberEdge, the CyberEdge will tunnel HTTP/HTTPS traffic to the upstream proxy. The upstream proxy then forwards the request to the intended destination on the Internet. Upon receiving the response, the upstream proxy relays it back to the CyberEdge proxy which in turn forwards the originating client. The use of upstream proxies may add significant latency to network connections and introduce complexity with troubleshooting connectivity issues between the client device and the Internet host.
This guide assumes you have a configured Ethernet network connection located in the Internet Zone. To configure an upstream proxy navigate to;
- Networks > Connections > Edit. It is strongly recommended that upstream proxy configurations only be applied to Network Connections in the Internet Zone.
- Click "Edit"
- Click "Add Upstream Proxy"
- Configure the upstream proxy
- Enable: Enabled the upstream proxy configuration
- Hostname/IP: Configure the hostname or IP address of the upstream proxy. Eg. fast.proxy-01.net
- Listening Port: The listening port of the upstream proxy. This should be provided by your upstream proxy service provider
- Username: The username of an account with permissions to use the upstream proxy server
- Password: The password of an account with permissions to use the upstream proxy
- Destination Ports: The destination ports of the upstream proxy. This must include 80/443 for HTTP and HTTPS traffic
- Click "Save"
- Click "Save" and "Apply changes"
HTTP/HTTPS traffic will now be tunnelled to the upstream proxy for the associated connection.
Important note
- A single network connection can accommodate up to 15 unique upstream proxy settings, allowing for the distribution of HTTP/HTTPS traffic across several proxies. This arrangement may be necessary in cases where the upstream proxy service lacks load balancing capabilities
- Only a single network connection can be configured with upstream proxy configurations. Multiple network connections with upstream proxy configurations is NOT supported
- For networks that require network traffic to be excluded from the upstream proxy connection, add a static route for the network against the relevant connection
- Applying upstream proxy configurations changes to a network connection is a disruptive process that involves the restart of several CyberEdge services including the proxy and DNS
- You should always check the upstream proxy server and associated credentials are working directly from your browser prior to configuring an upstream
Upstream Proxy in Balance and Failover Configurations
When upstream proxy configurations are integrated into regular network connections, these connections can be utilised within the Internet load balancing and failover setup. This setup enables the distribution of Internet traffic across both Direct Internet Access (DIA) connections and those connections set up with an upstream proxy depending on the requirements.
This guide assumes you have a active network connection with a working upstream proxy configuration located in the Internet Zone. To configure load balancing with an upstream proxy navigate to;
- Routing > Balance & Failover
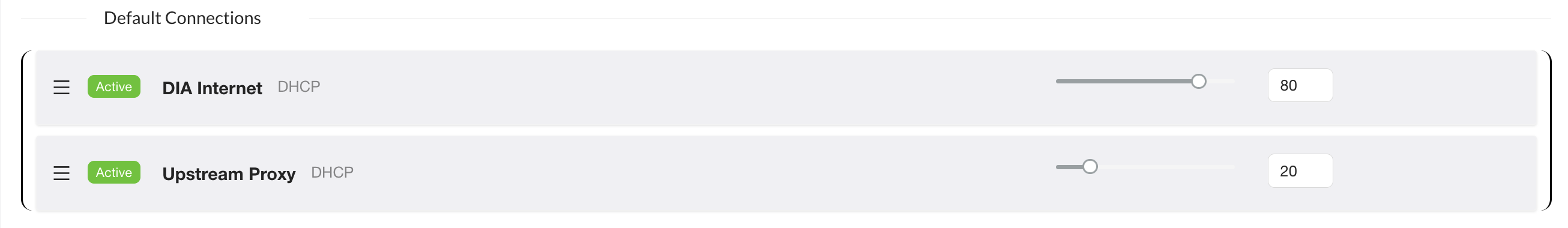
- In "Default Connections", add the network connections you wish to load balance
- To balance the load across configured connections effectively, it's important to assign appropriate weightings to each connection based on its speed and performance. The weighting determines the proportion of traffic that should be routed through each connection, with higher-weighted connections handling more traffic due to their superior speed or reliability.
- Click "Save" and "Apply changes"
In the following example, the majority of Internet traffic will be routed via the DIA Internet connection with the remainder routed via the upstream proxy connection.
PPPoE Connections
Point-to-Point Protocol over Ethernet (PPPoE) serves as a network protocol that wraps PPP frames within Ethernet frames, mainly utilised for broadband Internet access. It enables users to authenticate with an Internet Service Provider (ISP) through credentials, providing security and the benefit of a persistent connection. To configure a PPPoE Connection navigate to;
- Networks > Connections > Add > PPPoE Connection
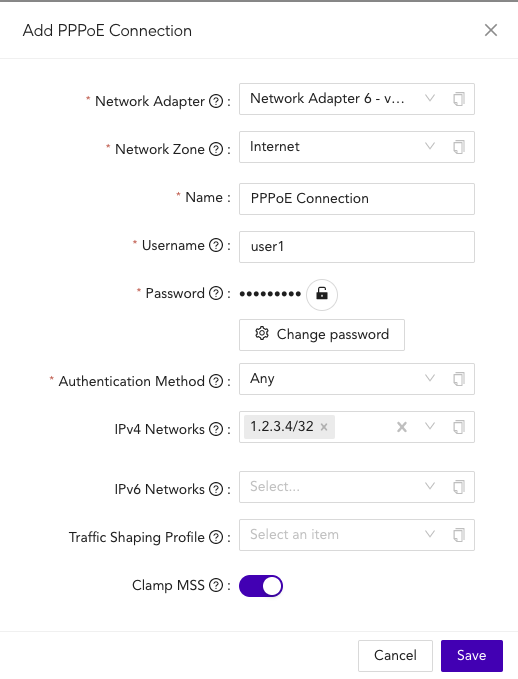
- Configure the PPPoE Connection
- Network Adapter: Select a network adapter port to be used by the PPPoE connection
- Network Zone: Specify a network zone for the connection. (This should almost always be the Internet Zone)
- Name: Provide a name for your network connection.
- Username: The username provided by your ISP for the PPPoE service
- Password: The password for the PPPoE service
- Authentication Method: The Authentication Method used by your ISP. The default recommendation is ANY
- IPv4 Networks: Specify an IPv4, or list of IP Address for the PPPoE network connection. This field requires a standard IPv4 CIDR format
- IPv6 Networks: Specify an IPv6, or list of IP Address for the PPPoE network connection
- Traffic Shaping Profile: Apply a traffic shaping profile if required. The default recommendation is to not apply a shaping policy
- Clamp MSS: Limit the Maximum Segment Size based on the path MTU. Recommended on for PPPoE connections
- Click "Save" and "Apply changes"
After establishing the new PPPoE network connection, it needs to be included in the load balancing and failover setup. To configure this navigate to:
- Routing > Balance & Failover
- The newly created PPPoE service will be listed under "Unused Connections"
- Move the PPPoE connection to the "default connections" section. If it's the sole configured connection, it will automatically serve as your default Internet connection. In the presence of multiple Internet connections, assign a weight to determine the PPPoE Internet Connection's priority
TCP/MSS Clamping for PPPoE
TCP MSS, or Transmission Control Protocol Maximum Segment Size, is a parameter specifying the maximum data that can be included in a single TCP segment. This parameter is particularly important in situations requiring data to be broken into smaller units for transmission over a network with a decreased Maximum Transmission Unit (MTU). When the size of a TCP segment exceeds the MTU of a specific network link, the data must be fragmented into smaller pieces to guarantee successful transmission. To configure TCP MSS clamping for an existing PPPoE network connection navigate to:
- Networks > Connection >
- Identify the PPPoE Connection that requires MSS clamping configured and click "Edit"
- Enable/Disable Clamp MSS
- Click "Save" and "Apply changes"
MSS clamping may be used to help resolve the following issues;
- Avoiding Fragmentation: Fragmentation can lead to performance degradation and increased latency. By adjusting the MSS to fit the smallest MTU along the path, MSS clamping ensures that packets are not fragmented, improving overall network performance
- Path MTU Discovery Issues: Path MTU Discovery (PMTUD) helps in determining the maximum packet size that can traverse a path without requiring fragmentation. However, PMTUD can fail if ICMP messages are filtered by firewalls or routers, leading to connectivity issues. MSS clamping can serve as a workaround by limiting TCP segment sizes to avoid fragmentation.
Client-to-Site VPN Subnet
Client-to-Site VPN networks utilize VPN subnets to establish connectivity. Before you can set up and deploy your VPN client, it's necessary to create a Client-to-Site VPN Subnet. Depending on the specifics of your network segmentation needs, this VPN Subnet can either be integrated into an existing local network zone or assigned to a newly created custom zone. To create a Client-to-Site VPN subnet navigate to:
- Network > Connections > Add > Client to Site VPN Subnet
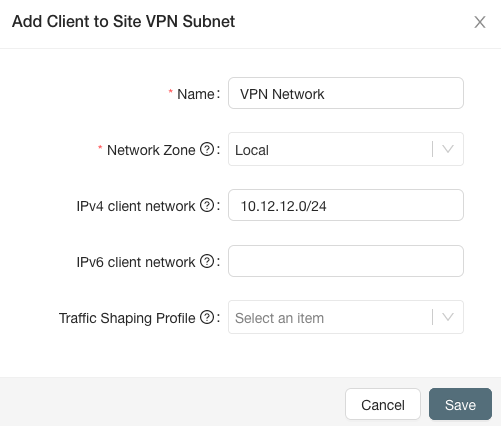
- Configure the connection
- Name: The name of the VPN subnet
- Network Zone: The network zone the VPN network will be added to
- IPv4 client Network: The network that will be used for VPN clients devices
- IPv6 client network: The network that will be used for VPN clients devices
- Traffic Shaping Profile: A traffic shaping profile to apply to the VPN Subnet. Default recommendation is no shaping
- Click "Save" and "Apply Changes"
More information on configuring the Clint-to-Site VPN can be found here
IPSec Connection
The CyberEdge IPSec can be set up as a conventional network connection, enabling the use of IPSec tunnels not only for secure Internet connectivity but also for load balancing and failover configurations. A comprehensive guide on configuring IPSec connections, can be found here